Published On Nov 17, 2022
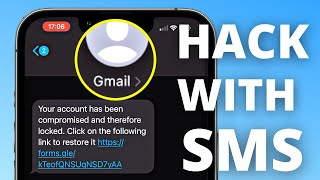
In recent years the data leaks have escalated, and leaked passwords and usernames have become a common attack vector in phishing attacks. Until recently phone numbers were commonly overlooked by attackers as well as red teams. This year has seen an increase in attacks circumventing text based 2fa.
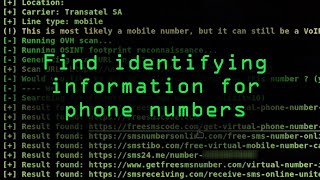
In this talk, the researchers will show how it's possible to gather data from publicly available sources and connect the phone numbers most likely used by two factor authentication systems to other leaked email and login credentials.
Presented by: Thomas Olofsson & Mikael Byström
Full Abstract and Presentation Materials: https://www.blackhat.com/us-22/briefi...