Published On Sep 15, 2023
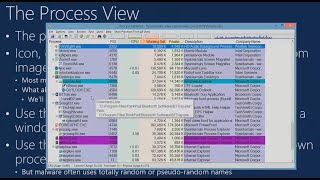
The signature update process is critical to EDR's effectiveness against emerging threats. The security update process must be highly secured, as demonstrated by the Flame malware attack that leveraged a rogue certificate for lateral movement. Nation-state capabilities are typically required for such an attack, given that signature update files are digitally signed by Microsoft.
We wondered if we could achieve similar capabilities running as an unprivileged user without possessing a rough certificate, instead we aimed to turn the original Windows Defender process to our full control.
In this talk we will deep dive into Windows Defender architecture, the signature database format and the update process, with a focus on the security verification logic. We will explain how an attacker can completely compromise any Windows agent or server, including those used by enterprises, by exploiting a powerful 0day vulnerability that even we didn't expect to discover.
We will demonstrate Defender-Pretender, a tool we developed to achieve neutralization of the EDR. allowing any already known malicious code to run Fully Un-Detected. It can also force Defender to delete admin’s data. OS and driver files, resulting in an unrecoverable OS. We will also explain how an attacker can alter Defender's detection and mitigation logic.